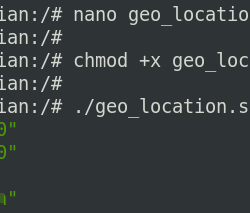
转储 是在命令行下运行的常见数据包分析器。 它允许用户拦截和显示通过计算机连接的网络传输或接收的 TCP/IP 和其他数据包。 在 BSD 许可下分发,[3] tcpdump 是免费软件。
转储 适用于大多数类 Unix 操作系统:Linux、Solaris、BSD、Mac OS X、HP-UX 和 AIX 等。 在这些系统中, 转储 使用 libpcap 库来捕获数据包。 tcpdump for Windows 的端口叫做 WinDump; 它使用 WinPcap,libpcap 的 Windows 端口。
如何在 Linux 中安装 tcpdump
在 Debian、Ubuntu、Mint linux 上安装 tcpdump u唱命令:
# sudo apt-get install tcpdump -y
安装 tcpdump Fedora, CentOS 和 RHEL linux 以下命令:
# yum install tcpdump
一次 转储 工具已安装在系统上,您可以继续浏览以下命令及其示例。
从特定接口捕获数据包
当你执行 tcpdump 命令 如果没有任何选项,它将捕获流经所有接口的所有数据包。 -i 选项与 转储 命令,允许您过滤特定的以太网接口。
# tcpdump -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:37:14.550522 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1578168831:1578169023, ack 3730519324, win 771, options [nop,nop,TS val 2916891 ecr 2882812], length 192 08:37:14.550713 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 541, options [nop,nop,TS val 2882823 ecr 2916891], length 0 08:37:14.551493 IP 192.168.1.80.48393 > resolver1.opendns.com.domain: 23054+ PTR? 88.1.168.192.in-addr.arpa. (43) 08:37:14.597605 IP resolver1.opendns.com.domain > 192.168.1.80.48393: 23054* 0/1/0 (102) 08:37:14.598305 IP 192.168.1.80.37674 > resolver1.opendns.com.domain: 36143+ PTR? 80.1.168.192.in-addr.arpa. (43) 08:37:14.649412 IP resolver1.opendns.com.domain > 192.168.1.80.37674: 36143* 0/1/0 (102) ...
仅捕获 N 个数据包
当你 执行 tcpdump 命令 它提供数据包,直到您取消 tcpdump 命令. 使用 -c 选项可以指定要捕获的数据包数量。
# tcpdump -c 2 -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:38:57.023840 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1578778495:1578778687, ack 3730520300, win 771, options [nop,nop,TS val 3019365 ecr 2908433], length 192 08:38:57.024187 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 1233, options [nop,nop,TS val 2908441 ecr 3019365], length 0 2 packets captured 6 packets received by filter 0 packets dropped by kernel
以 ASCII 格式打印捕获的数据包
下列 转储 语法以 ASCII 格式打印数据包。
# tcpdump -A -i eth0 -c 2 tcpdump:抑制详细输出,使用 -v 或 -vv 进行完整协议解码侦听 eth0,链接类型 EN10MB(以太网),捕获大小 65535 字节 08:41:42.839829 IP 192.168。 1.80.ssh > 192.168.1.88.52274:标志 [P.], seq 1580671503:1580671695, ack 3730522172, win 771, options [nop,nop,TS val 3185181 ecr 2949887], 长度 192 [email protected]@......P...X...2^7"...[@<........... .0...-..Jr..x...p&y8*c....0i.....o...;h.I.0.R][email protected];.z..}... .Dk....A...*....>....By....>........M ...m..y..u..u;i..T.,P.....;u`.....i.?......q. VF.'.U 08:41:42.840144 IP 192.168.1.88.52274 > 192.168.1.80.ssh:标志 [.], ack 192, win 1792, 选项 [nop,nop,TS val 2949895 ecr 3185181], 长度 0 [email protected]@..#...X...P.2...[@<^7"......[..... .-...0.. 2 packets captured 6 packets received by filter 0 packets dropped by kernel
Display Captured Packets in HEX and ASCII using tcpdump -XX
Some users might want to analyse the packets in hex values. tcpdump provides a way to print packets in both ASCII and HEX format.
# tcpdump -XX -i eth0 -c 2
Display Available Interfaces
To list number of available interfaces on the system, run the following command with -D option.
# tcpdump -D 1.eth0 2.usbmon1 (USB bus number 1) 3.usbmon2 (USB bus number 2) 4.any (Pseudo-device that captures on all interfaces) 5.lo
Capture the packets and write into a file using tcpdump -w
tcpdump allows you to save the packets to a file, and later you can use the packet file for further analysis.
# tcpdump -w file.pcap -i eth0 tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 10 packets captured 10 packets received by filter 0 packets dropped by kernel
Reading the packets from a saved file using tcpdump -r
You can read the captured pcap file and view the packets for analysis, as shown below.
# tcpdump -r file.pcap reading from file file.pcap, link-type EN10MB (Ethernet) 08:48:42.977710 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1580681775:1580681903, ack 3730526668, win 771, options [nop,nop,TS val 3605318 ecr 3054921],长度 128 08:48:42.978087 IP 192.168.1.88.52274 > 192.168.1.80.ssh:标志 [.], ack 128, win 1792, 选项 [nop,nop,TS val 3054930 ecr 3605318], 长度 0 08:48:48.189810 IP 192.168.1.253.nfs > 239.255.255.250.ssdp: UDP, 长度 330 08:48:49.939291 IP 192.168.1.253.nfs > 239.255.255.250.ssdp [P.], seq 1:49, ack 128, win 1792, 选项 [nop,nop,TS val 3056670 ecr 3605318], 长度 48
捕获IP地址数据包
在上述所有示例中,它打印带有 DNS 地址的数据包,而不是 ip 地址。 以下示例捕获数据包,并将显示所涉及机器的 IP 地址。
# tcpdump -n -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:52:03.880624 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1581156671:1581156863, ack 3730531052, win 771, options [nop,nop,TS val 3806222 ecr 3105148], length 192 08:52:03.881068 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 3308, options [nop,nop,TS val 3105155 ecr 3806222], length 0 08:52:03.881825 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 192:560, ack 1, win 771, options [nop,nop,TS val 3806223 ecr 3105155], length 368 08:52:03.882112 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 560, win 3331, options [nop,nop,TS val 3105156 ecr 3806223], length 0
仅捕获 TCP 数据包。
抓包基于 TCP 端口,使用选项运行以下命令 通讯协议.
# tcpdump -i eth0 tcp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:53:59.609774 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1581594191:1581594383, ack 3730533372, win 771, options [nop,nop,TS val 3921951 ecr 3134081], length 192 1 packets captured 5 packets received by filter 0 packets dropped by kernel
从特定端口捕获数据包
假设您要捕获特定端口 22 的数据包,通过指定端口号执行以下命令 22 如下所示。
# tcpdump -i eth0 port 80 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:55:31.321096 IP 192.168.1.88.44209 > 192.168.1.80.http: Flags [S], seq 3335310211, win 14600, options [mss 1460,sackOK,TS val 3157015 ecr 0,nop,wscale 7], length 0 08:55:31.321737 IP 192.168.1.88.44210 > 192.168.1.80.http: Flags [S], seq 185161599, win 14600, options [mss 1460,sackOK,TS val 3157016 ecr 0,nop,wscale 7], length 0 08:55:31.378373 IP 192.168.1.88.44211 > 192.168.1.80.http: Flags [S], seq 2915876395, win 14600, options [mss 1460,sackOK,TS val 3157030 ecr 0,nop,wscale 7], length 0 ^C 3 packets captured 3 packets received by filter 0 packets dropped by kernel
从源 IP 捕获数据包
从源捕获数据包 知识产权,假设您要捕获数据包 192.168.0.2,使用命令如下。
# tcpdump -i eth0 src 192.168.1.88 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:57:23.275553 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 1582390207, win 6516, options [nop,nop,TS val 3185004 ecr 4125616], length 0 08:57:23.365741 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 193, win 6516, options [nop,nop,TS val 3185026 ecr 4125706], length 0 08:57:23.367421 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 385, win 6516, options [nop,nop,TS val 3185027 ecr 4125708], length 0 08:57:23.368405 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 577, win 6516, options [nop,nop,TS val 3185027 ecr 4125709], length 0 ... 223 packets captured 223 packets received by filter 0 packets dropped by kernel
从目标 IP 捕获数据包
从目的地捕获数据包 知识产权,假设您要捕获数据包 50.116.66.139,使用命令如下。
# tcpdump -i eth0 dst 192.168.1.1 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:58:57.790236 IP 192.168.1.80 > 192.168.1.1: ICMP echo request, id 54280, seq 1, length 64 08:58:58.791754 IP 192.168.1.80 > 192.168.1.1: ICMP echo request, id 54280, seq 2, length 64 08:58:59.793019 IP 192.168.1.80 > 192.168.1.1: ICMP echo request, id 54280, seq 3, length 64 ^C 3 packets captured 3 packets received by filter 0 packets dropped by kernel